Danger of token theft! Why it is a big concern
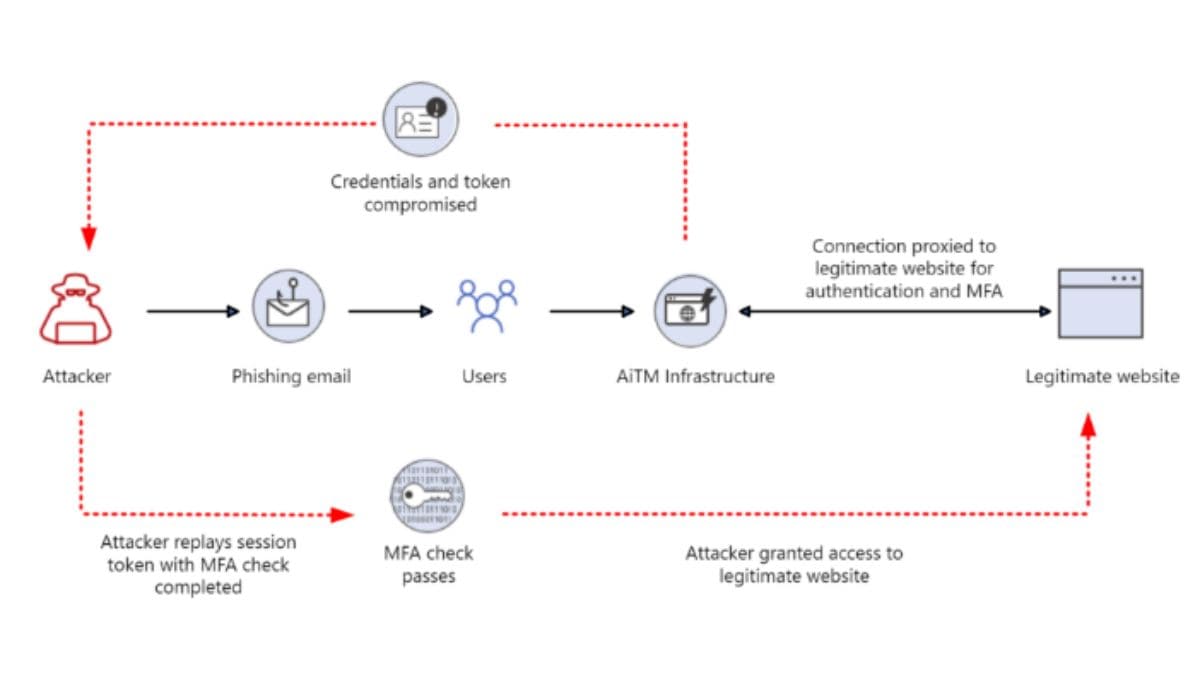
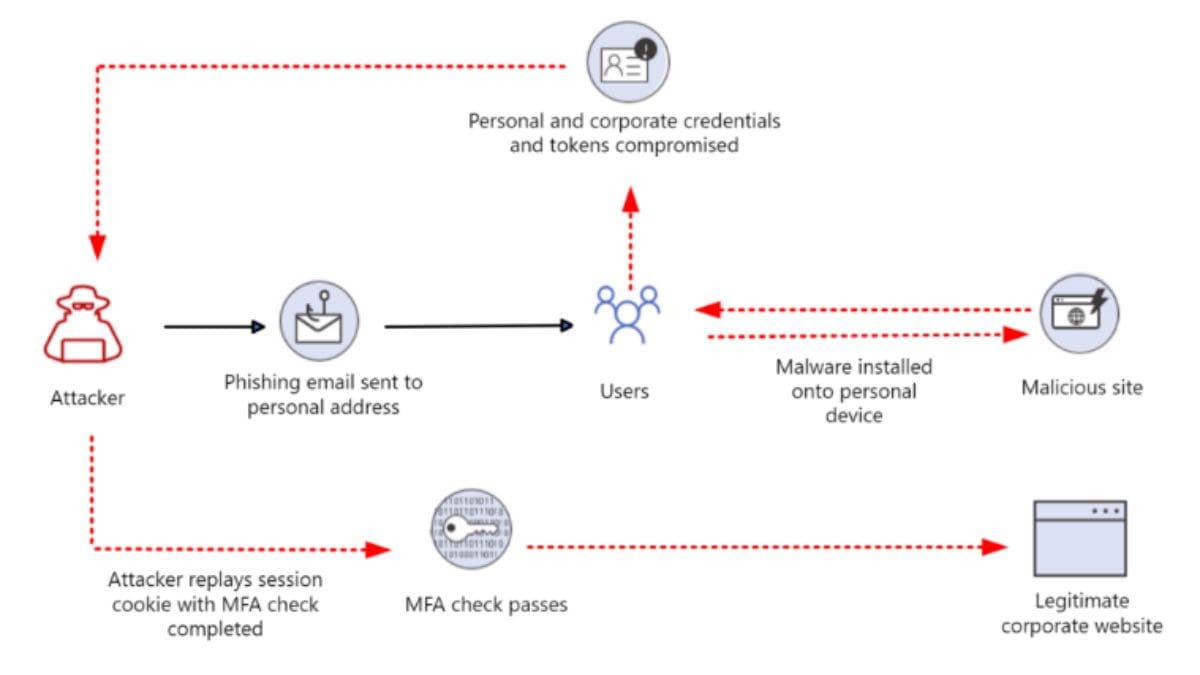
Cybercriminals are continually discovering new methods to infiltrate online security measures. One of the latest tactics is token theft! What is it? How does it work and how does it affect you? Here’s everything you need to know.











First Published Date: 03 Mar, 13:10 IST
Tags:
cyber crime
cybersecurity
NEXT ARTICLE BEGINS