Breaking down NSO Group’s Pegasus spyware, WhatsApp’s video-calling vulnerability
WhatsApp claims Israel-based surveillance firm NSO Group exploited vulnerability in video-calling feature to hack users’ accounts.


WhatsApp on Thursday sued Israel-based surveillance firm NSO Group for allegedly hacking the messaging platform to spy on about 1,400 users. The targeted users included activists, journalists, and senior government officials among others. WhatsApp alleged that NSO Group exploited a vulnerability in its video-calling feature to conduct the cyber attacks.
WhatsApp and its users have long been targeted by hackers around the world despite the instant messaging app boasts of highly secure end-to-end encryption. From GIFs to spoofing user identity, hackers have adopted innovative ways to hack users' accounts. In the case of the latest NSO Group, WhatsApp traced the cyberattack to a May 2019 incident where the vulnerability allowed hackers to remotely install spyware. Malicious actors used 'Pegasus', a popular spying tool offered by the Israel firm.
What is Pegasus?
Pegasus is believed to be one of the most sophisticated spyware in the world. The spyware can hack both iOS and Android devices by targeting vulnerabilities in the operating systems. It is capable of running in the background without the targeted user ever knowing about the hack. Once the spyware is installed on a device, it accesses critical and private data of users such as contacts, messages, passwords, and even live voice calls. It can also remotely switch on the affected device's camera and microphone.
"Other vectors used in prior cases of NSO targeting include tricking targets into clicking on a link using social engineering. For example, in 2017, the wife of a murdered Mexican journalist was sent alarming text messages concerning her husband's murder, designed to trick her into clicking on a link and infecting her phone with the Pegasus spyware," wrote Citizen Lab in a blog post.
"Pegasus and its variants (collectively, "Pegasus") were designed to be remotely installed and enable the remote access and control of information—including calls, messages, and location—on mobile devices using the Android, iOS, and BlackBerry operating systems," said WhatsApp in its lawsuit against the NSO Group.
"According to media reports and NSO documents, Defendants [NSO Group] claimed that Pegasus could be surreptitiously installed on a victim's phone without the victim taking any action, such as clicking a link or opening a message (known as remote installation). Defendants promoted that Pegasus's remote installation feature facilitated infecting victims' phones without using spearphishing messages that could be detected and reported by the victims," it added.
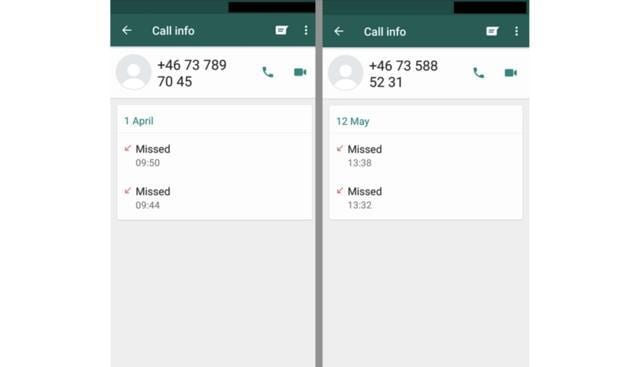

Hacking via video calling
The exploit, now fixed, allowed malicious actors to hack WhatsApp by just making a video call. The targeted user didn't even need to receive the video call to be infected. Facebook later confirmed that WhatsApp vulnerability occurred due to a rather common bug known as buffer overflow.
Buffer overflow essentially refers to an anomaly wherein data overflows to other parts of memory and overwrites adjacent memory location. Hackers can use the exploit to inject malicious code and acquire access to a device.
"A buffer overflow vulnerability in WhatsApp VOIP stack allowed remote code execution via specially crafted series of RTCP packets sent to a target phone number," Facebook said after fixing the exploit.
"The issue affects WhatsApp for Android prior to v2.19.134, WhatsApp Business for Android prior to v2.19.44, WhatsApp for iOS prior to v2.19.51, WhatsApp Business for iOS prior to v2.19.51, WhatsApp for Windows Phone prior to v2.18.348, and WhatsApp for Tizen prior to v2.18.15," it added.
Catch all the Latest Tech News, Mobile News, Laptop News, Gaming news, Wearables News , How To News, also keep up with us on Whatsapp channel,Twitter, Facebook, Google News, and Instagram. For our latest videos, subscribe to our YouTube channel.