WannaCry ransomware attack: Follow these steps and keep your data safe
An unprecedented global cyber attack infected computers in at least 150 countries beginning last Friday
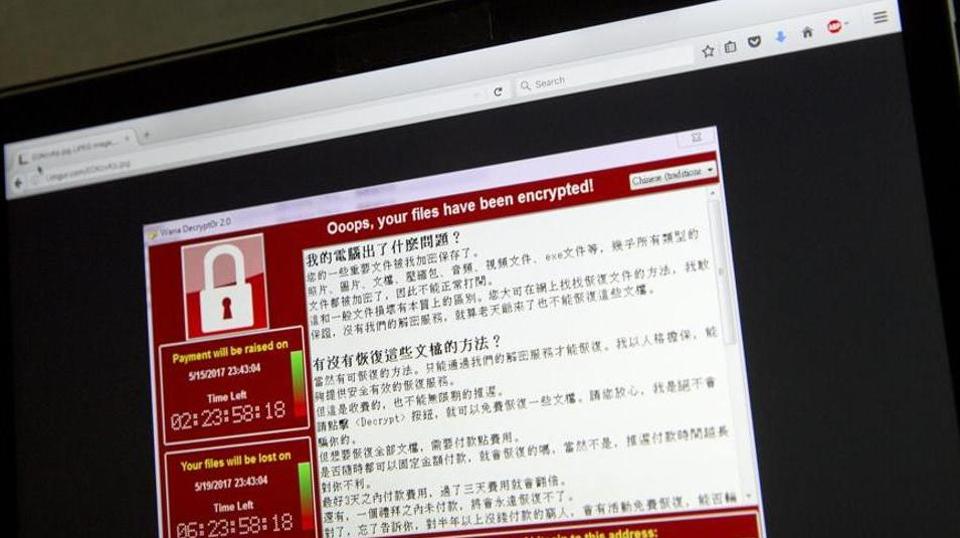
Computers across the world were locked up and users' files held for ransom when dozens of countries were hit in a cyberattack that targeted hospitals, companies and government agencies. Here's all you need to know how malware and ransomware work and what you need to do to your data safe.
What is ransomware?
It is a type of malware that essentially takes over a computer and prevents users from accessing data on it until a ransom is paid in bitcoins.
How does your computer become infected with ransomware?
In most cases, the software infects computers through links or attachments in malicious messages known as phishing emails. The software usually is hidden within links or attachments in emails. Once the user clicks on the link or opens the document, their computer is infected and the software takes over.
What kind of files are being targeted?
- Commonly used office file extensions (.ppt, .doc, .docx, .xlsx, .sxi)
- Less common and nation-specific office formats (.sxw, .odt, .hwp)
- Archive and media files (.zip, .rar, .tar, .bz2, .mp4, .mkv)
- Emails and email databases (.eml, .msg, .ost, .pst, .edb)
- Database files (.sql, .accdb, .mdb, .dbf, .odb, .myd)
- Developers' source code and project files (.php, .java, .cpp, .pas, .asm)
- Encryption keys and certificates (.key, .pfx, .pem, .p12, .csr, .gpg, .aes)
- Files used by graphic designers, artists and photographers (.vsd, .odg, .raw, .nef, .svg, .psd)
- Virtual machine files (.vmx, .vmdk, .vdi)
How can you prevent an attack?
1. Apply the patches to the Windows systems recommended by Microsoft Security Bulletin MS17-010.
2. Maintain updated antivirus software.
3. Keep and regularly update an offline database of important files. Ideally, backups of data should be maintained on separate devices.
4. Organisations connecting to the Internet through Enterprise Edge or perimeter network devices [UDP 137, 138 and TCP 139, 445] should block their SMB ports or disable SMBv1.
5. Users and administrators of older Windows systems such as Windows XP, Vista, Server 2008, and Server 2003 should get an update to a newer version.
Some other practices that will help keep your data safe:
* Establish an email validation system. These prevent spam and detect phishing emails, the most common tool used by ransomware attacks..
* Disable or block spam in your mailbox. Don't open attachments in suspicious and unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in such an e-mail, even if the link seems benign.
* Deploy web and email filters on your network. Configure these devices to scan for known bad domains, sources, and addresses; block these before receiving and downloading messages. Scan all emails, attachments, and downloads with a reputable antivirus program both on the host and at the mail gateway.
* Disable macros in Microsoft Office products. Some Office products allow for the disabling of macros that originate from outside of an organization and can provide a hybrid approach when the organization depends on the legitimate use of macros. On Windows, specific settings can block macros originating in the Internet from running.
* Configure access controls including file, directory, and network share permissions with least privilege in mind.
* Block attachments of the following file types: exe|pif |tmp |url|vb|vbe|scr|reg| cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
* Enable personal firewalls on individual workstations.
How to know if your system has been infected and what to do?
* If you notice that any of the files listed above or the extensions of other important files have changed to (*.wnry), then you are already infected.
* Do not pay the ransom, as this does not guarantee the files will be released. Report such instances of fraud to CERT and law enforcement agencies.
* Disconnect all network connections and external storage immediately.
* Shut down your computer and inform your organisation's IT department.
* Keep your backups ready before experts assist you.
Catch all the Latest Tech News, Mobile News, Laptop News, Gaming news, Wearables News , How To News, also keep up with us on Whatsapp channel,Twitter, Facebook, Google News, and Instagram. For our latest videos, subscribe to our YouTube channel.


























