Secure your data through cloud services, just follow these 5 practices
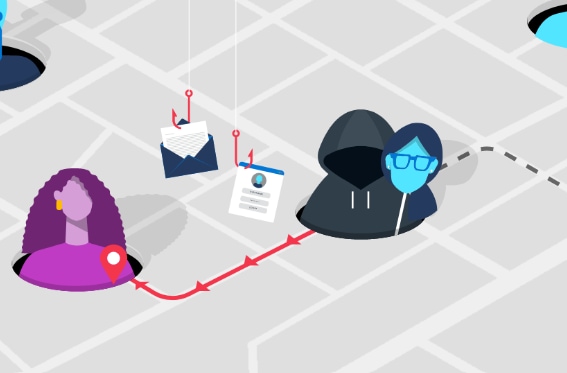
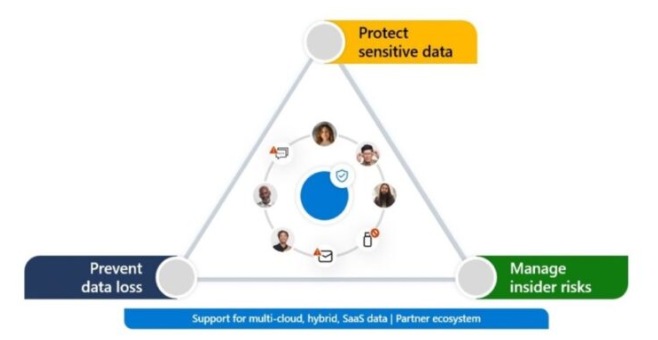
Are you looking for ways to secure data through cloud services? Then just look at this list of 5 practices suggested by Microsoft Security to secure data in cloud services to stop cyberattacks.







First Published Date: 31 Jul, 17:26 IST
Tags:
microsoft
NEXT ARTICLE BEGINS