Bluetooth vulnerability puts millions of devices at risk: Here’s what you should do
The loophole found in Bluetooth allows cyber criminals to intercept and decrypt and/or forge and inject device messages. Here’s everything you need to know about the Bluetooth vulnerability.

A new vulnerability found in commonly available Bluetooth has put millions of devices on risk. The vulnerability allows a cyber criminal to intercept and monitor the data exchanged from a device in proximity. This loophole affects devices from Broadcom, Qualcomm, Intel, and Apple among others. Many Android handsets may also be at risk.
Bluetooth SIG, the official regulator for Bluetooth wireless technology, earlier this week published a detailed report about the vulnerability in two Bluetooth features - Secure Simple Pairing and LE Secure Connections.
What is the loophole?
"The researchers identified that the Bluetooth specification recommends, but does not require, that a device supporting the Secure Simple Pairing or LE Secure Connections features validate the public key received over the air when pairing with a new device. It is possible that some vendors may have developed Bluetooth products that support those features but do not perform public key validation during the pairing procedure. In such cases, connections between those devices could be vulnerable to a man-in-the-middle attack that would allow for the monitoring or manipulation of traffic," Bluetooth SIG said on its website.
"For an attack to be successful, an attacking device would need to be within wireless range of two vulnerable Bluetooth devices that were going through a pairing procedure. The attacking device would need to intercept the public key exchange by blocking each transmission, sending an acknowledgement to the sending device, and then injecting the malicious packet to the receiving device within a narrow time window. If only one device had the vulnerability, the attack would not be successful."
How does it work?
According to CERT, a cyber criminal within the range of the affected device may be able to leverage "a man-in-the-middle network" position to find out "cryptographic keys" users by the device. The criminal can then access monitor and modify the device content.
"Bluetooth utilizes a device pairing mechanism based on elliptic-curve Diffie-Hellman (ECDH) key exchange to allow encrypted communication between devices. The ECDH key pair consists of a private and a public key, and the public keys are exchanged to produce a shared pairing key. The devices must also agree on the elliptic curve parameters being used. Previous work on the "Invalid Curve Attack" showed that the ECDH parameters are not always validated before being used in computing the resulted shared key, which reduces attacker effort to obtain the private key of the device under attack if the implementation does not validate all of the parameters before computing the shared key," said CERT on its website.
"In some implementations, the elliptic curve parameters are not all validated by the cryptographic algorithm implementation, which may allow a remote attacker within wireless range to inject an invalid public key to determine the session key with high probability. Such an attacker can then passively intercept and decrypt all device messages, and/or forge and inject malicious messages."
The reason these attack works is that, in order to communicate, pairing needs to be done for communication between both the devices, then they agree on a certain parameter. Following which they produce their keys and while making a connection the Bluetooth devices don't validate the parameters properly or sufficiently, explains Rahul Tyagi, Co-Founder & VP, Lucideus.
"For a hacker to hack or sniff the bluetooth connection or network, the hacker's bluetooth device through which the attack would be conducted needs to be in range of both the victim bluetooth devices. Hacker's bluetooth device must also intercept the key exchanges between the victim bluetooth devices and that can only be done by blocking the transmission, sending an acknowledgement packet to the sending device and then injecting malicious packet to the receiving device. This needs to be done within a certain amount of time. Both the devices need to be vulnerable for this attack to work," he added.
Who has been affected?
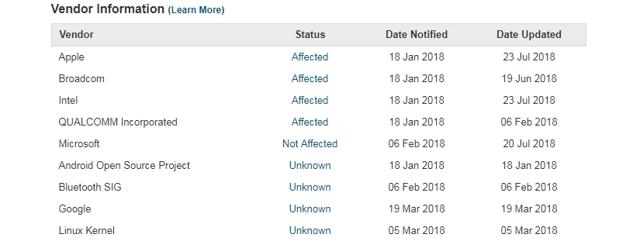
According to the CERT list, devices from Apple, Intel and Qualcomm have been affected by the Bluetooth vulnerability. It is worth noting that Apple and Intel have already released firmware and software updates to fix the vulnerability. It is not known whether Google, Android Open Source Project (AOSP) and Linux have also been affected. Microsoft isn't part of the list.

What should users do?
If you're using a Qualcomm or Apple device, you should immediately install the latest firmware or software update.
"While there are no confirmed mass reports of the newly discovered Bluetooth vulnerability being exploited on scale, this vulnerability could be taken of advantage of silently if consumers are not using the patched version over time. As Bluetooth is a globally used framework, it's a very attractive target for hackers and its scale and spread enhances its vulnerability," said Farrhad Acidwalla, founder of CYBERNETIV, an enterprise-security focused company.
"From an affected end user's security viewpoint, wistfully there is not much one can do except to make sure they are on the latest software update from their manufacturer or alternatively turn off Bluetooth if their device is susceptible and has not received an update," he added.
Rahul recommends that users should keep Bluetooth turned off if they're not in use. "By doing this user's can avoid unwanted pairing or connections, also when Bluetooth is left on Bluetooth packets are broadcasted which contains Bluetooth hardware details which make it easier to track the victim so by turning Bluetooth off users can avoid being tracked or hacked. And they should make sure that they are updated with the latest security updates released by the manufacturer," he said.
Catch all the Latest Tech News, Mobile News, Laptop News, Gaming news, Wearables News , How To News, also keep up with us on Whatsapp channel,Twitter, Facebook, Google News, and Instagram. For our latest videos, subscribe to our YouTube channel.