Google warns researchers targeted by North Korean hackers via social media
The team said the attackers seemed to target only Windows systems, while users who were running updated Windows 10 and Chrome browsers were still infected, suggesting the attacks were previously undetected - also known as zero day vulnerabilities.

Google's Threat Analysis Group (TAG) has warned that it has discovered a relatively new campaign over the last several months that targeted security researchers and other members of the infosec community across several companies.
The team at Google believes that the attacks were carried out by a government-backed entity based in North Korea, Google TAG's Adam Weidemann said in a blog post on Monday.
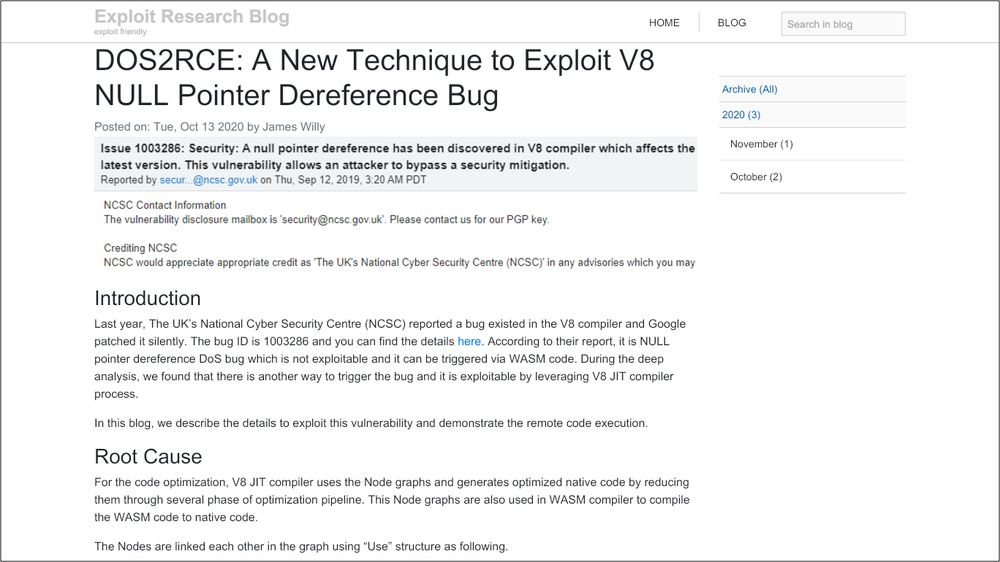
As the infosec community is usually wary of suspicious looking accounts or sources of information, the attackers had created a ‘research blog' and set up multiple Twitter accounts which they then used to get in touch with their targets - the researchers. Those accounts disseminated posts made to the research blog, which were then retweeted by other accounts to give them a sense of credibility and amplify them, the threat analysis team said.
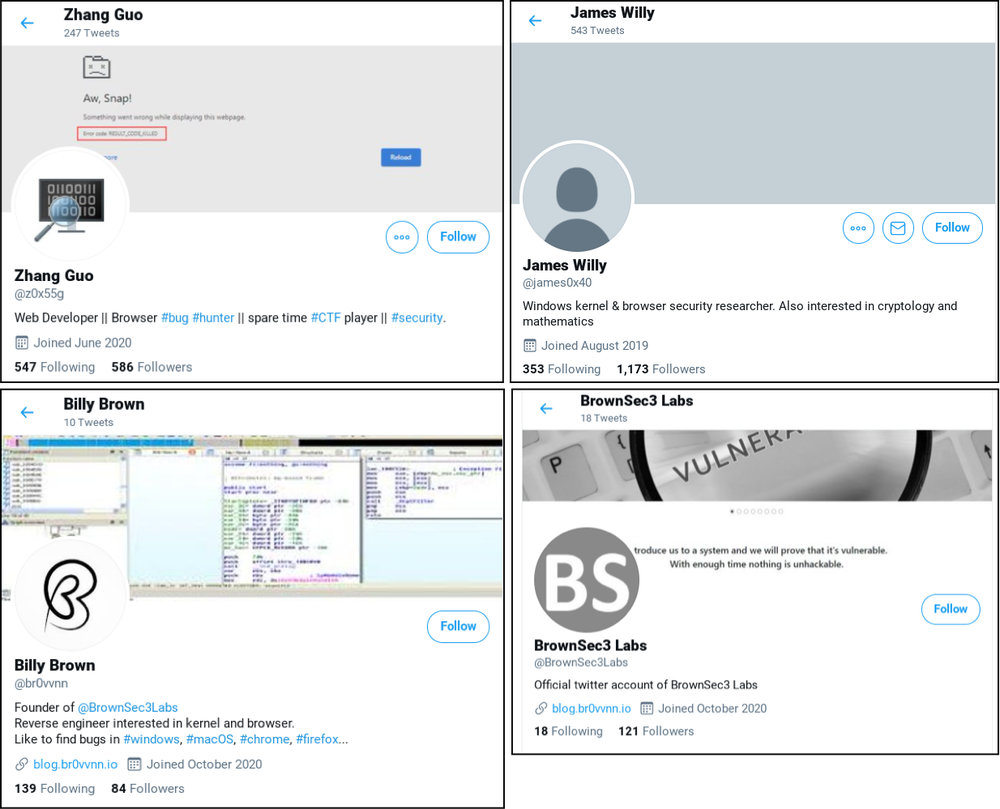

What's interesting is that while the attackers' blog had analyses of publicly disclosed vulnerabilities, they also managed to convince legitimate security researchers to contribute as ‘guests' to their site, perhaps luring them with the promise of a good platform to be featured on and a chance to network with other researchers. The researchers were contacted on Twitter, LinkedIn, Telegram, Discord and Keybase.
Also read: Chrome for Android gets another zero-day vulnerability fix
Those who agreed to collaborate were sent a Visual Studio Project, which would infect the targeted researcher's computer and install a backdoor access for another malware controlled server, then wait for commands from the main server. Google says the attackers seemed to target only Windows systems. Also, users who were running updated Windows 10 and Chrome browsers were still infected, suggesting the attacks were previously undetected - also known as zero day vulnerabilities.

“We hope this post will remind those in the security research community that they are targets to government-backed attackers and should remain vigilant when engaging with individuals they have not previously interacted with,” Weidemann. “If you are concerned that you are being targeted, we recommend that you compartmentalize your research activities using separate physical or virtual machines for general web browsing, interacting with others in the research community, accepting files from third parties and your own security research,” he added.
Catch all the Latest Tech News, Mobile News, Laptop News, Gaming news, Wearables News , How To News, also keep up with us on Whatsapp channel,Twitter, Facebook, Google News, and Instagram. For our latest videos, subscribe to our YouTube channel.